Whereas the load of propaganda seems to have eased up a bit of in latest months, proof reveals there’s far more to return.
Paperwork obtained by investigative journalists Michael Shellenberger, Alex Gutentag and Matt Taibbi from an nameless however “extremely credible” whistleblower reveals new particulars on how the U.S. censorship-industrial advanced — a community of greater than 100 authorities companies, non-public corporations, academia and nonprofits — polices and criminalizes “wrong-think.”1
Explosive Revelations
The brand new cache of paperwork, known as the “CTIL recordsdata,” which refers back to the Cyber Risk Intelligence League, have been launched by the three journalists in late November 2023.
“A whistleblower has come ahead with an explosive new trove of paperwork, rivaling or exceeding the Twitter Information and Fb Information in scale and significance,” the trio wrote on their Substack, “Public.”2
“They describe the actions of an ‘anti-disinformation’ group referred to as the Cyber Risk Intelligence League, or CTIL, that formally started because the volunteer venture of knowledge scientists and protection and intelligence veterans however whose techniques over time seem to have been absorbed into a number of official initiatives, together with these of the Division of Homeland Safety (DHS).
The CTI League paperwork provide the lacking hyperlink solutions to key questions not addressed within the Twitter Information and Fb Information. Mixed, they provide a complete image of the beginning of the ‘anti-disinformation’ sector, or what we now have referred to as the Censorship Industrial Advanced.”
The paperwork describe how the fashionable digital censorship applications have been created, and the varied roles of the navy, U.S. intelligence companies, civil society organizations and business media.
In addition they describe the strategies and methods used, such because the creation and use of sock puppet accounts to spy on and steer on-line discussions and propagate desired narratives, the discrediting of dissenters, and the intentional weaponization of the monetary business towards the identical.
In keeping with the whistleblower, CTIL was additionally concerned within the creation of a counter-disinformation venture to “stop a repeat of 2016,” a reference to Brexit and Donald Trump’s shock election win — two conditions through which the democratic processes really received out.
As famous by Jimmy Dore within the video above, this was not about stopping the circulation of false data. It was to make sure that no political outsider will ever be capable to get into the Oval Workplace once more. The instruction to forestall a repeat of 2016 was a direct name to undermine, if not eradicate, the method of free and honest elections.
Importantly, the paperwork admit that censorship efforts towards Individuals should be completed by companions within the non-public sector, as a result of the federal government does not have the “authorized authority” to take action.
The CTIL
The brand new cache of paperwork and movies reveal that 2019 was a pivotal yr for the censorship-industrial advanced. In keeping with Public,3 that’s when “U.S. and U.Okay. navy and intelligence contractors led by a former U.Okay. protection researcher, Sara-Jayne ‘SJ’ Terp, developed the sweeping censorship framework.”
These contractors turned co-leaders of the CTIL, the unique founders of which included a former Israeli intelligence official, Ohad Zaidenberg, Microsoft safety supervisor Nate Warfield, Chris Mills, one other Microsoft safety officer, and Marc Rogers, the pinnacle of safety operations for the hackers conference, DEF CON.
In keeping with media articles,4 these extremely expert and in-demand professionals made the altruistic determination to volunteer their providers to assist billion-dollar hospitals with their cybersecurity, freed from cost, no strings hooked up. It wasn’t a reputable cowl story then, and it positive hasn’t aged any higher.
Inside one month of the CTIL’s founding in March 2020, this supposedly all-volunteer group had grown to 1,400 “by invitation solely” members in 76 international locations and formally partnered with the U.S. Division of Homeland Safety’s Cybersecurity and Info Safety Company (CISA). As reported by Public:5
“The CTIL framework and the public-private mannequin are the seeds of what each the US and UK would put into place in 2020 and 2021, together with masking censorship inside cybersecurity establishments and counter-disinformation agendas; a heavy concentrate on stopping disfavored narratives, not simply improper information; and pressuring social media platforms to take down data or take different actions to forestall content material from going viral.”
Parallel Censorship Agendas
Within the spring of 2020, CISA additionally created the Election Integrity Partnership (EIP) — a consortium made up by the Stanford Web Observatory (SIO), the College of Washington’s Middle for an Knowledgeable Public, the Atlantic Council’s Digital Forensic Analysis Lab, and Graphika (a social media analytics firm) — and outsourced what would in any other case be unlawful and unconstitutional censorship to it.
Throughout the 2020 election cycle, the EIP and CISA labored with the State Division’s World Engagement Middle (GEC) and the DHS-backed Elections Infrastructure Info Sharing and Evaluation Middle (EI-ISAC) to affect and police political discussions on-line. The EIP coordinated the take-down of undesirable content material utilizing a real-time chat app that the DHS, EIP and social media firms all share.6
On the similar time, the CTIL was monitoring and reporting anti-lockdown views on social media. A “legislation enforcement” channel was created particularly to spy on and monitor social media customers who posted anti-lockdown hashtags. CTIL even saved a spreadsheet with particulars from their Twitter bios.
In keeping with Public, the CTIL additionally “engaged in offensive operations to affect public opinion, discussing methods to advertise ‘counter-messaging,’ co-opt hashtags, dilute disfavored messaging, create sock puppet accounts, and infiltrate non-public invite-only teams.” In February 2021, the EIP was rebranded because the Virality Challenge, at which level their focus of censorship shifted from elections to COVID-related issues.
Authorities Infiltration and Take-Over
Whereas one CTIL member, Bonnie Smalley, replied to a question by Public saying the CTIL “had nothing to do with the federal government,” the proof reveals in any other case. No less than a dozen of presidency workers who labored with the DHS, FBI and CISA have been additionally lively members of CTIL.
In keeping with the whistleblower, the CTIL’s aim “was to grow to be a part of the federal authorities.” Terp’s plan was to arrange “MisinfoSec communities” that would come with the federal sector, and the paperwork present this purpose was achieved. In April 2020, Chris Krebs, then-director of CISA, additionally publicly introduced the company’s partnership with CTIL.
Public continues:7
“The paperwork additionally present that Terp and her colleagues, by means of a bunch referred to as MisinfoSec Working Group, which included [Stanford Internet Observatory research manager Renee] DiResta, created a censorship, affect, and anti-disinformation technique referred to as Adversarial Misinformation and Affect Ways and Strategies (AMITT).
They wrote AMITT by adapting a cybersecurity framework developed by MITRE … Terp later used AMITT to develop the DISARM framework, which the World Well being Group then employed in ‘countering anti-vaccination campaigns throughout Europe.’
A key part of Terp’s work by means of CTIL, MisinfoSec, and AMITT was to insert the idea of ‘cognitive safety’ into the fields of cybersecurity and knowledge safety …
The ambitions of the 2020 pioneers of the Censorship Industrial Advanced went far past merely urging Twitter to slap a warning label on Tweets, or to place people on blacklists.
The AMITT framework requires discrediting people as a mandatory prerequisite of demanding censorship towards them. It requires coaching influencers to unfold messages. And it requires attempting to get banks to chop off monetary providers to people who manage rallies or occasions.”
Weaponization of Finance Sector Originated With CTIL
So, now we all know the place the weaponization of the monetary sector got here from. It originated with the CTIL, which expressly sought to get banks to “reduce off monetary providers to people who manage rallies or occasions.”
Clearly, as evidenced by my very own case and plenty of others, banks and on-line cost processors have additionally been enticed into reducing providers for individuals who merely expressed opposing views. It isn’t simply rally organizers which can be being focused.
Beneath the Cowl of Altruism
Whereas CTIL officers have repeatedly careworn that the group was based on purely altruistic ideas, the clear aim of its leaders was to “construct help for censorship amongst nationwide safety and cybersecurity establishments,” Public writes, they usually constructed that help by selling Terp’s concept of “cognitive safety.”
The selection of the time period “cognitive safety” takes on a moderately sinister taste in gentle of Dr. Michael Nehls’ findings that there’s been what seems to be an intentional effort to destroy the autobiographical reminiscence operate within the brains of the general public over the previous 4 years, thereby facilitating mass indoctrination and inhibiting private will and important considering.
He presents his thesis within the e-book “The Indoctrinated Mind: Easy methods to Efficiently Fend Off the World Assault on Your Psychological Freedom,”8 revealed in mid-December 2023.
The whistleblower’s materials clearly reveal that subtle navy techniques have been turned on the American public, highly effective psychological instruments — the very instruments Nehls says can actually alter organic mind operate.
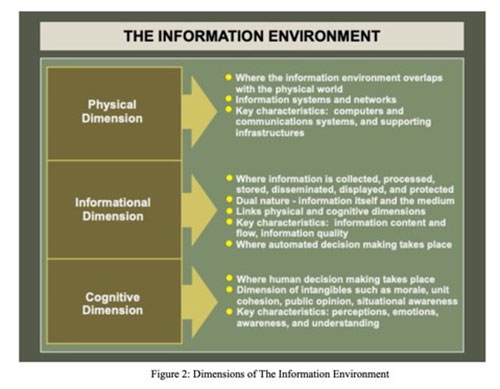
Public cites a MisinfoSec report through which “The authors referred to as for putting censorship efforts inside ‘cybersecurity’ even whereas acknowledging that ‘misinformation safety’ is totally completely different from cybersecurity. They wrote that the third pillar of ‘The data surroundings’ after bodily and cybersecurity must be ‘The Cognitive Dimension.’”
Certainly, your thoughts — your cognition, your very potential to assume independently — is the battlefield of right now’s battle, as Nehls proposes in his e-book. The horrifying half is that the instruments employed even have the facility to reprogram who you might be.
We’re certainly “hackable animals,” as proposed by Yuval Noah Harari, and the censorship-industrial advanced has been hacking into the very mind construction of billions of individuals for the final 4 years already. Gutentag even touches on this in a December 3, 2023, article:9
“What was as soon as thought-about a ‘conspiracy concept’ that navy and intelligence forces have been manipulating public opinion by means of inorganic interventions, has now been confirmed.
Our examine of the Censorship Industrial Advanced has uncovered a far-reaching plan to subvert the democratic course of and interact in actions which have a foundation in navy methods and that are tantamount to makes an attempt at thought or thoughts management.”
‘It’s Authorized if We Can Get Away With It’
The CTIL recordsdata additionally present there was a transparent intent to avoid the First Modification by outsourcing censorship to the non-public and nongovernmental sector. In keeping with the whistleblower:10
“The ethos was that if we get away with it, it’s authorized, and there have been no First Modification issues as a result of we now have a ‘public-private partnership’ — that’s the phrase they used to disguise these issues. ‘Personal individuals can do issues public servants can’t do, and public servants can present the management and coordination.’”
Good Information, Dangerous Information
The excellent news is that an increasing number of data is popping out in regards to the U.S. authorities’s unlawful outsourcing of censorship, and with it, authorized challenges that throw up blocks towards this circumvention of the Structure.
We’ve additionally had different victories. In August 2022, the DHS was compelled to terminate the Disinformation Governance Board resulting from public backlash. CISA has additionally deleted details about home censorship work from its web site, and has dismantled its Misinformation, Disinformation, and Malinformation (MDM) subcommittee.
The Choose Subcommittee on the Weaponization of the Federal Authorities can also be persevering with its seek for fact, and can (hopefully) use no matter energy at its disposal to rein within the abuse. Its most up-to-date report, “The Weaponization of ‘Disinformation’ Pseudo-Specialists and Bureaucrats: How the Federal Authorities Partnered with Universities to Censor Individuals’ Political Speech”11 was revealed November 6, 2023.
Sadly, we even have a worldwide effort underway to not solely normalize but in addition legalize this type of third-party censorship. In an August 1, 2023, video (beneath), Mike Benz12 defined this technique.
The “Middleware” Plan To Restructure The Censorship Business
1. Middleware=”censorship as a service” orgs
2. Morphing from top-down to middle-out
3. Regs + middleware = disinfo compliance market pic.twitter.com/lDPqH72HrD
— Mike Benz (@MikeBenzCyber) August 1, 2023
In brief, they’re attempting to restructure the censorship business “away from a top-down government-driven mannequin” to a “aggressive middleware mannequin” the place “content material curation” (learn censorship) is just outsourced to third-party organizations.
This fashion, a “authorized” disinformation compliance market is created whereas authorities can declare it has nothing to do with the management of knowledge. Mainly, what we’re taking a look at is the emergence of organized company censorship.
There’s no clear answer to this menace, apart from to proceed pushing again towards any and all efforts to legalize, standardize and normalize censorship. To vocally object, to refuse utilizing middleware like NewsGuard, and to boycott any firm or group that makes use of middleware or engages in censorship of any type.

